Why the Internet isn’t secure – To understand how Tor is able to protect a user’s identity as they browse the Internet, it seems prudent to discuss exactly how the Internet works. The Internet is, at its most basic, the series of connections between computers across a great distance. In the beginning, computers were isolated, unable to communicate with each other. As the tech got more advanced, engineers were able to physically link computers together, creating early networks.
These networks still required the computers to be relatively near each other, however. Eventually, advances in fiber optics enabled networks to connect across continents, allowing for the Internet to be born.
Some computers house the data stored on the Internet, including web pages like Google. These computers are known as “servers.” A device used to access this information, such as a smartphone or PC, is known as a client. The transmission lines that connect clients to servers come in a variety of forms, whether fiber optic cables or wireless signals, but they are all connections.
Although clients initiate connections to get information from servers, the flow goes both ways.
Data is exchanged across the Internet in packets. These packets contain information about the sender and the destination, and certain individuals and organizations can use this data to monitor who is doing certain things or accessing certain information on the Web.
It is not just the server that can see this data. Traffic analysis is big business, and many organizations, both private and governmental, can monitor the messages flowing between clients and servers. How, then, does Tor keep the user’s information secret?
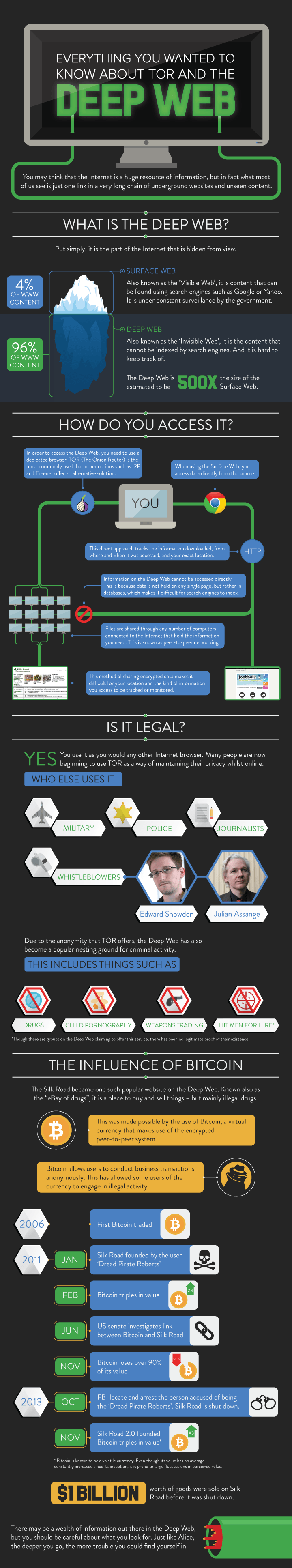
How Tor has the answer
There are two key aspects to onion routing. First, the Tor network is composed of volunteers who use their computers as “nodes.” As mentioned earlier, during normal browsing, information travels across the Internet in packets. When a Tor user visits a website, however, their packets do not simply travel to that server. Instead, Tor creates a path through randomly assigned nodes on that the packet will follow before reaching the server.