About Tor: It is free software for enabling anonymous communication. The name is derived from an acronym for the original software project name “The Onion Router”. Tor directs Internet traffic through a free, worldwide, volunteer network consisting of more than seven thousand relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult for Internet activity to be traced back to the user: this includes “visits to Web sites, online posts, instant messages, and other communication forms”.
Tor’s use is intended to protect the personal privacy of users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities from being monitored.
An adversary might try to de-anonymize the user by some means. One way this may be achieved is by exploiting vulnerable software on the user’s computer. The NSA had a technique that targets a vulnerability – which they codenamed “EgotisticalGiraffe” – in an outdated Firefox browser version at one time bundled with the Tor package, and in general, targets Tor users for close monitoring under its XKeyscore program.
Attacks against Tor are an active area of academic research, which is welcomed by the Tor Project itself.
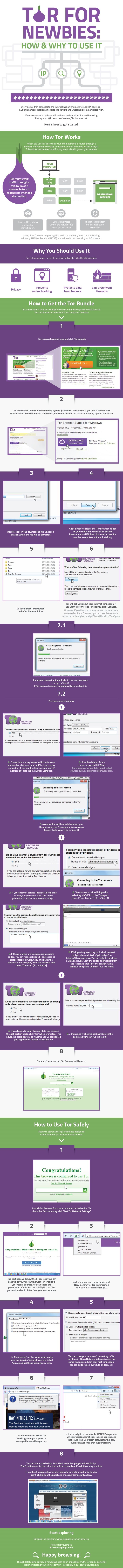
The core principle of Tor, “onion routing”, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson and computer scientists Michael G. Reed and David Goldschlag, with the purpose of protecting U.S. intelligence communications online. Onion routing was further developed by DARPA in 1997.