Tor is a private anonymous browser that aims to conceal its user’s identities and their online activity from traffic and surveillance by separating identification and routing. Tor web browser is an implementation of onion routing, which encrypts and then randomly bounces communications through a network of relays run by volunteers around the globe.
Tor is said to be an “Onion Router” because it layers your traffic like an onion which is a free network or nodes that connect. Using Tor, you can hide your IP address and browse the deep web and dark where the server runs anonymously.
But Tor doesn’t replace your VPN (Virtual Private Network), as it effectively anonymizes your browsing experience.
Connecting Tor with a VPN is the best way to protect your internet privacy and security.
Also Read: What are the benefits of using Tor? Why you need them?
The Tor network is a group of volunteer-operated servers which mainly focuses on the user privacy and security and they employs this network by connecting through a serious of visual tunnels rather than making a direct connection. This type of method allows both the individuals and the organizations to share information over public networks without compromising their privacy.
By using Tor, you can reach the blocked destination or content or resources. It is also used as building blocks for a software developer to create a new communication tool with built-in privacy features. Among the market, Tor browser is said to be an effective censorship circumvention tool.
In the world of darkness, we are unable to protect yourself from the threat. We all surf the internet in a normal and standard search engines like Google, Yahoo, and Bing. But, do you know what? there is also the other existence of search engines available on the internet which is completely hidden in the darkness. The hidden web is called the “Deep Web“. It is not crawled by any popular search engine and it is not visible to the public. You can access them only if you are a member of Deep Web.
Related: What do you mean by “Deep Web”? And why is it hidden?
The above article could help you to know the facts about the deep web and its importance. You need to use Tor while you surf the deep web links which are more dangerous and creepy.
What is Tor Project?
Tor Project or Org is derived from an acronym for the original software project name “The Onion Router”. Tor directs Internet traffic through a free, worldwide, volunteer network consisting of more than seven thousand relays to conceal a user’s location and usage from anyone conducting network surveillance or traffic analysis.
Does Tor browser make us truly anonymous?
Yes, of course, they do. But not in all the circumstances. Tor can’t solve all anonymity problems. It focuses on protecting the transport of data.
- Don’t provide your name or other revealing information in web forms.
- Be aware that, like all anonymizing networks that are fast enough for web browsing, Tor does not provide protection against end-to-end timing attacks: If your attacker can watch the traffic coming out of your computer, and also the traffic arriving at your chosen destination, he can use statistical analysis to discover that they are part of the same circuit.
- To avoid this risk factor, you need to have a powerful VPN (Virtual Private Network) on your system before accessing the web.
Using Tor network isn’t enough for protection, you need ultra-security services like CyberGhost VPN to remain anonymous on the internet. Limited time Offer! Get this deal Now!
I strongly recommend our user to run a premium VPN rather than a free version to protect yourself from the hack. Without a VPN, it is unsafe to surf the dark deep web.
This tool is used for anonymous communication purpose and you can use this as an individual or a group.
Why individuals\Groups use Tor?
Individuals: They use Tor to keep their websites from tracking or to connect to new sites, instant messaging services, or the like when these are blocked by their local internet providers.
- Tor is one of the best private browsers on the market to remain anonymous online.
- It hides your original IP address by connecting to different nodes.
- You need privacy, right? That’s the reason behind the Tor development.
There are more Tor like browsers available online such as I2P and Freenet. But, these are not providing enough security to the user to prevent them from the hack.
Tor private browser won’t reveal your actual location of the place from which you access.
A journalist uses Tor to safely communicate with whistleblowers and dissidents. And a Non-governmental organization use this anonymous tools to allow their workers to connect to their home website from abroad, without notifying anybody.
Groups members use Tor for safeguarding their privacy and security online. Indymedia and Electronic Frontier Foundation recommends Tor as a mechanism for maintaining civil liberties online. Corporate use this tool to conduct competitive analysis and to protect sensitive procurement patterns from eavesdroppers.
Why we need Tor?
By using Tor network, you can easily hide your IP address which protects you against from internal surveillance known as “Traffic analysis”.Traffic analysis will reveal your public network information which means your source and destination of internal traffic (Behaviour and Interest) can be tracked. But we don’t need to get tracked by anyone. To hide all your behavior data from the public, you need to have a special software called “Tor”.
Tor can prevent you from hack and allows the user to hide their original IP location from they access. Moreover, it connects to several unique nodes before connecting to the network, this enables them to hide their user IP address.
Related: The best guide to access the Deep web using Tor browser
It is great to surf the hidden world (Deep web and Dark web) with the combination of Tor and VPN. Let’s see the working procedure of Tor browser in reality.
How does Tor browser work?
Before understanding what TOR does and how it works, it will be nice if you understand how the internet works on a basic level.
In general two end systems communicate directly, via their IP addresses. When you search a website via the browser, DNS servers return you an IP address. Then your browser sends your request to the corresponding server of that IP address.
The packet formed by your device contains your IP address as source and server’s IP address (the one you are communicating with) as a destination. This helps intermediate nodes (mostly routers) to forward your packet to the destination (it is not important for you to know how routers perform this task). Thus, communicating nodes always know who they are communicating. Other information (like cookies) provided by your browser to the server also helps them to know who you are.
A bit more information on this topic is provided here. Follow the three-way working guidance of Tor.
Method 1:
Initially, the server needs to tell about its existence to the internet.
Then the server randomly picks TOR nodes and build a circuit around them, and then ask them to act as introduction points (nodes) by giving them its public key.
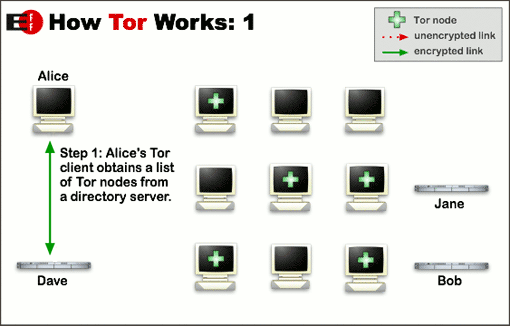
Tor helps to reduce the risks of both simple and sophisticated traffic analysis by distributing your transactions over several places on the Internet, so no single point can link you to your destination. The idea is similar to using a twisty, hard-to-follow route in order to throw off somebody who is tailing you — and then periodically erasing your footprints. Instead of taking a direct route from source to destination, data packets on the Tor network take a random pathway through several relays that cover your tracks so no observer at any single point can tell where the data came from or where it’s going.
To create a private network pathway with Tor, the user’s software or client incrementally builds a circuit of encrypted connections through relays on the network. The circuit is extended one hop at a time, and each relay along the way knows only which relay gave it data and which relay it is giving data to. No individual relay ever knows the complete path that a data packet has taken. The client negotiates a separate set of encryption keys for each hop along the circuit to ensure that each hop can’t trace these connections as they pass through.
Method 2:
Once a circuit has been established, many kinds of data can be exchanged and several different sorts of software applications can be deployed over the Tor network. Because each relay sees no more than one hop in the circuit, neither an eavesdropper nor a compromised relay can use traffic analysis to link the connection’s source and destination. Tor only works for TCP streams and can be used by any application with SOCKS support.
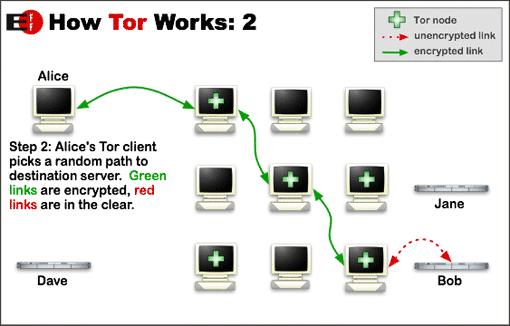
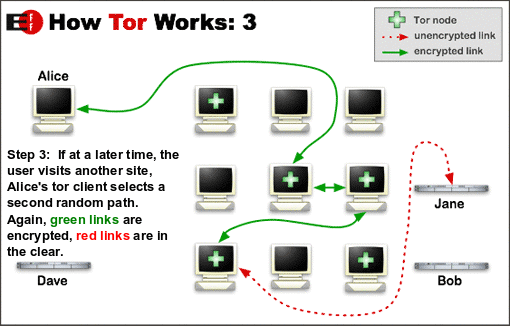
For efficiency, the Tor software uses the same circuit for connections that happen within the same ten minutes or so. Later requests are given a new circuit, to keep people from linking your earlier actions to the new ones.
Do’s and Don’ts of Tor
- Use Tor Browser: It is recommended to use Tor browser on your system before getting access to the dark web and its hidden wiki links. It protects your privacy and keeps you remain anonymous online.
- Don’t torrent over Tor: The torrent file seems to be ignoring proxy settings and make a direct connection even when they use Tor. It is because they send your original IP address in the tracker GET request. By this way, the torrent files will work. So, stop downloading or accessing the torrent file over Tor. It should be strictly avoided.
- Don’t install and enable browser plugins: By using the browser plugin, your anonymity will get affected. And you will no more be anonymous online. Browser plugins like Flash, RealPlayer, Quicktime, and others are used to bypass Tor. I don’t recommend enabling browser plugins on Tor browser.
- Use HTTPS versions of websites: Tor will encrypt your traffic within their network, but the encryption to the destination website depends upon that website. Tor browser uses HTTPS everywhere to force the use of encryption. Always use this HTTPS version.
- Don’t open documents downloaded through Tor while online: It is not recommended to open the DOC and PDF files which are been downloaded through Tor while online. This may severely affect your privacy and reveal your original IP. In case, if you need to open the DOC and PDF file on Tor. we strongly recommend either using a disconnected computer, downloading the free VirtualBox and using it with a virtual machine image with networking disabled or using Tails. Under no circumstances is it safe to use BitTorrent and Tor together,
- Use Bridges: Some of your internal traffic isn’t been watched by Tor as default. To prevent his risk, use a Tor bridge relay rather than connecting directly to the public.
Where can I download Tor if it is blocked in some countries?
It is possible to download Tor from GetTor service if your country blocks Tor project and its mirror. If not, you can directly download from Torproject.org.
There is a two-way possibility for you to download Tor browser via Email and Twitter. You can download this browser for Windows, Linux, and OS-X (Mac OS X).
Tor for Android: Also download Orbot, the Tor browser for Android on Google play store.
Tor for iOS: Tor isn’t available for the iOS device. You can expect the release in future.
Tor for Tails: Go to this link.
Download Tor Browser via Email
The user can communicate with GetTor robot by sending an email to download Tor. The well-known email address to do is [email protected].
If you send them a request, then you will get links to download Tor browser from popular cloud service like Dropbox. Download the file and install them on your device to browse anonymously online.
Download Tor Browser via Twitter
You can also download Tor via Twitter by sending them a direct message to @get_tor account.
Is it legal to use the Tor network?
Using Tor is not a crime factor or illegal for normal usage. You can hide your original IP address and the browsing history by using Tor. But most of the people use Tor to remain anonymous on the internet because they are doing illegal things. If you use Tor for any illegal purpose, then it is illegal. Be safe and be smart.
Even with Tor, You are still at risk
Not in all the case, you are protected. Even Tor isn’t safe to browse the web on some occasion.
To avoid risk: You are recommended to use our tested VPN service on your system to remain anonymous online.
Other Related Article:




Spotter says
tell me what do you think about VPN with open source like OpenVPN GUI? i use the VPN and server vpngate.net and suppose OpenVPN GUI is much better than similar to Nord VPN so on..
deepwebadmin says
OpenVPN is not that encrypted and could be easily broken and doesn’t have stability and performance as NordVPN.